Structured support for platform automation and security in regulated IT environments.
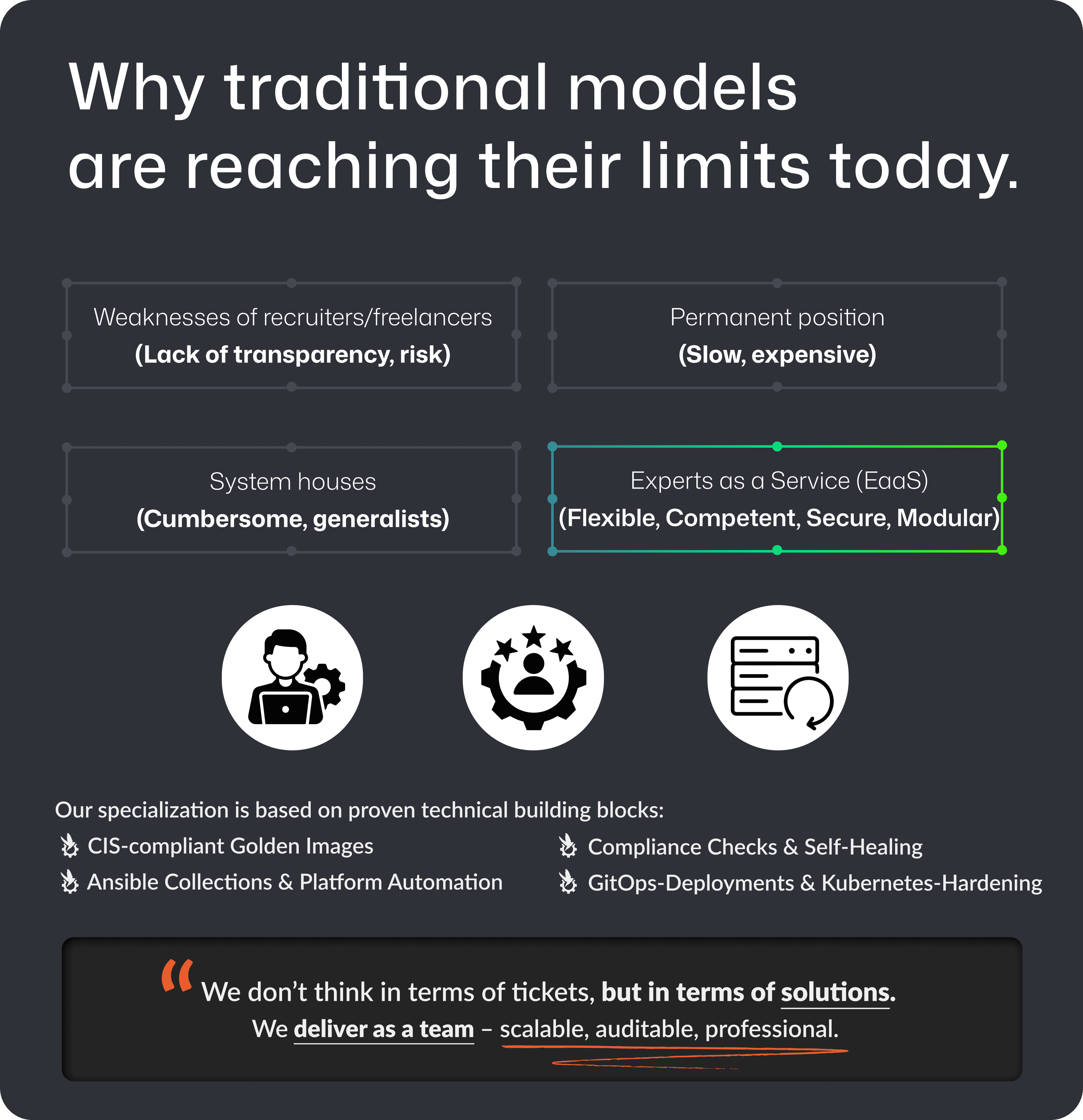
EaaS is designed for organizations that want to evolve their IT platforms in a secure and traceable way. They do not want to build new permanent roles in the short term. They also do not want to outsource responsibility completely.
Our experts support teams for a limited time in clearly defined task areas. Integrated, fully documented, and with a strong focus on sustainable results.
Experts as a Service (EaaS) is a support model for companies that want to use external expertise in a targeted and controlled manner—without traditional outsourcing or permanent dependencies.
The focus is not on providing individual people, but on responsible participation in clearly defined areas such as platform automation, security, or compliance.
The goal of EaaS is to relieve existing teams, build knowledge, and create results that are documented, traceable, and sustainable in the long term.
EaaS combines external expertise with internal responsibility—in a structured, time-limited, and transparent manner.
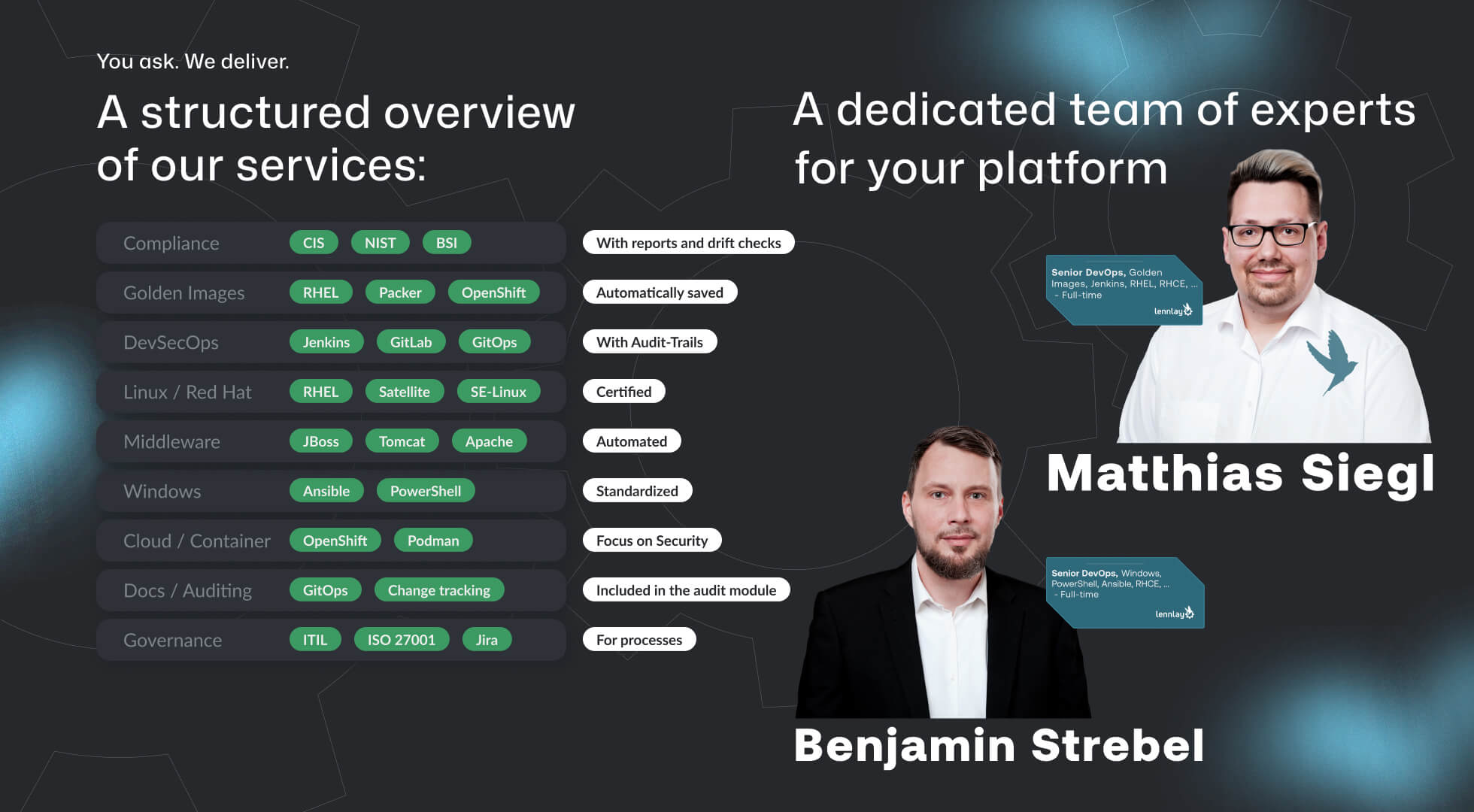
Our experts have many years of experience in enterprise and regulated IT environments.
They work based on standards, document everything, and aim to build knowledge inside the company without creating new dependencies.
Step 1: Needs assessment
Technical scoping & boundaries
Step 2: Onboarding
Structured integration into your systems
Step 3: Implementation
Responsible collaboration in defined areas
Step 4: Completion & Handover
Documentation & Knowledge transfer
EaaS targets organizations that need temporary expertise in automation, security, or compliance – without building new roles or outsourcing responsibility.
Especially suitable for audit preparation, platform stabilization, or skill gaps in existing teams.
Particularly suitable for:
The smart way to secure, scalable IT excellence.
Engineering as a Service: controlled, secure, scalable.
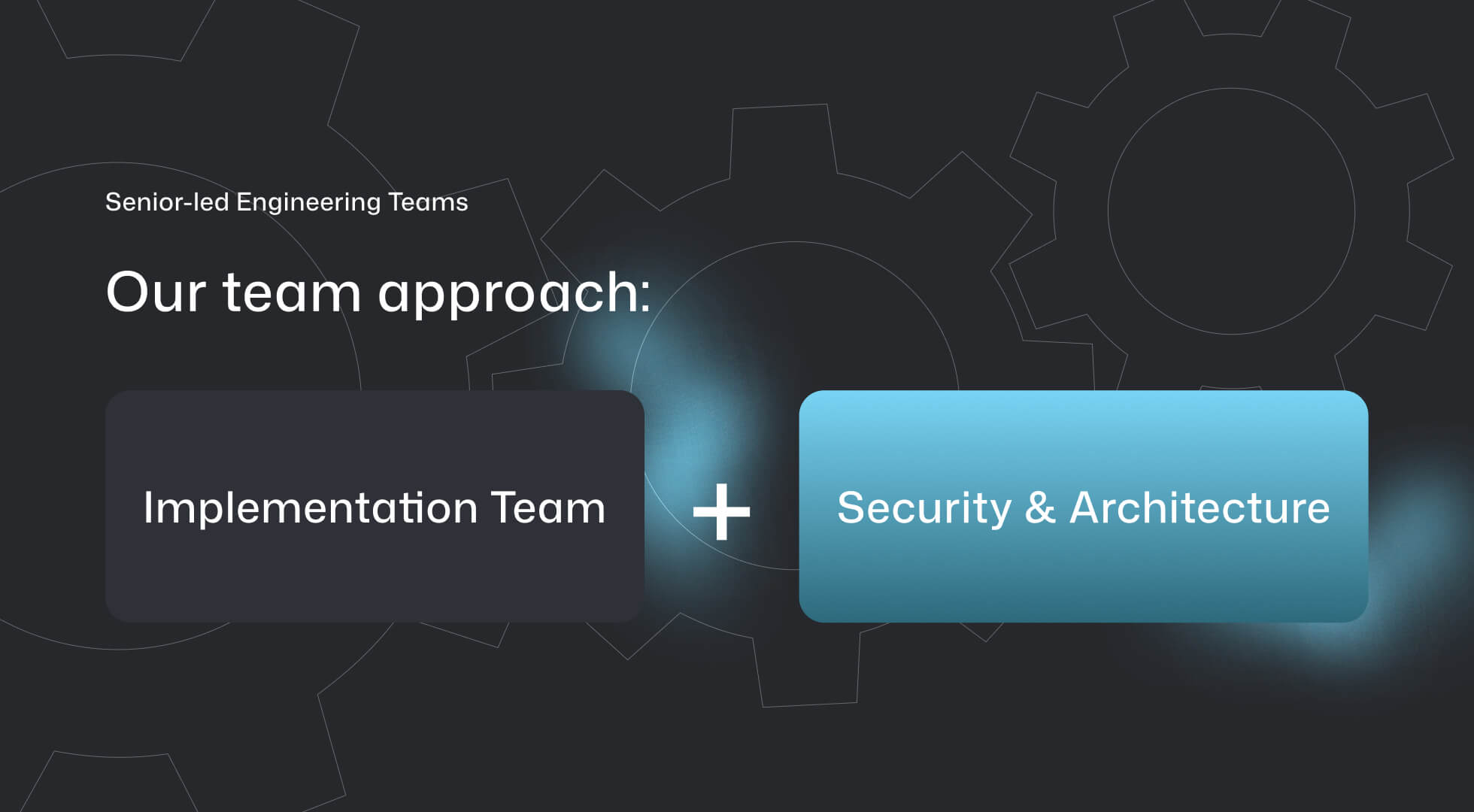
Senior-led Engineering Teams
Architecture, security and technical responsibility rest with experienced senior engineers. Implementation happens through clearly defined engineering resources – structured, documented and controlled.